Work
Home | Work | Play | Photos | Contact | About
Security Notes
Home \ Work \ Security Engineering
Vulnerability Timeline
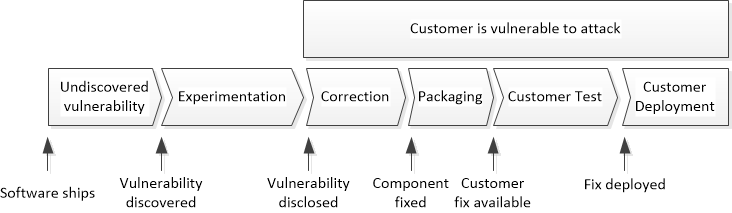
Customers typically test vulnerability patches before deploying them - this is nonsensical. It is better to patch a vulnerable system, even though this may adversely affect existing systems. Deploy security patches as you get them - systems are more at risk by not patching than having a system fail because of the patch. Also consider the reputational damage caused by compromise when a patch is already available...
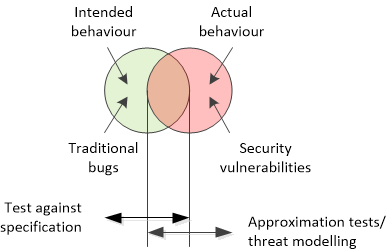
Vulnerability test strategy
Document, Segment and Restrict (DSR)
- Document...
- Model apps and services
- Environment dependencies
- Segment...
- Apps
- Security requirements
- Restrict...
- Disable services
- Close ports
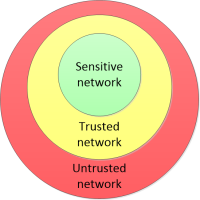
Segmentation and Isolation
Segmentation isolates and secures resources by sensitivity. The website would live in the outer-most circle. User access control sytems in the middle, and sensitive services in the inner-most circle.
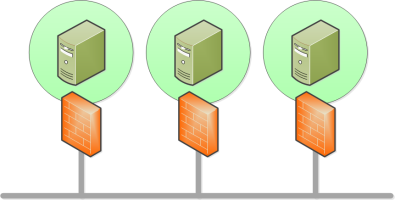
Isolate all shared resources in your network with dedicated firewalls and access control lists.
See also:
All content copyright © Michael Wittenburg 1995 to 2025. All rights reserved.
Merch (t-shirts designed by my twin)
